Zero-Trust Security Models: How to Implement Them in 2025
Traditional perimeter-based protection is insufficient as cyber threats become more complex and dispersed. Zero-Trust Security Models are becoming more and more popular in 2025—not as a choice, but as a strategic must. With clarity, speed, and quantifiable outcomes, Techo Lab has assisted businesses of all sizes in integrating Zero-Trust concepts into their infrastructure.
This blog explores the current meaning of Zero-Trust and, more crucially, how to successfully use it by 2025.
A Zero-Trust Security Model: What Is It?
Never trust, always verify is the straightforward but effective tenet of a zero-trust security model. Zero-Trust makes the assumption that every person, device, and system—whether inside or outside the network—could be hacked, in contrast to traditional models that presume everything within a network is secure.
This strategy necessitates comprehensive visibility throughout your IT ecosystem, stringent access constraints, and ongoing authentication. It lessens the effect of breaches when they do happen and shrinks the attack surface.
The Significance of Zero-Trust in 2025

Zero-Trust Security Models are essential in the modern world for a number of reasons:
- Remote and hybrid work is permanent; the risk increases with the number of endpoints.
- Standard cloud-native stacks no set perimeter.
- Insider threats and ransomware are on the rise; implicit trust is no longer reliable.
- There is growing regulatory pressure; compliance necessitates a stronger security posture.
Simply put, 2025 is the year to abandon antiquated firewalls and begin creating systems with no presumptions.
Important Guidelines for Implementing Zero-Trust
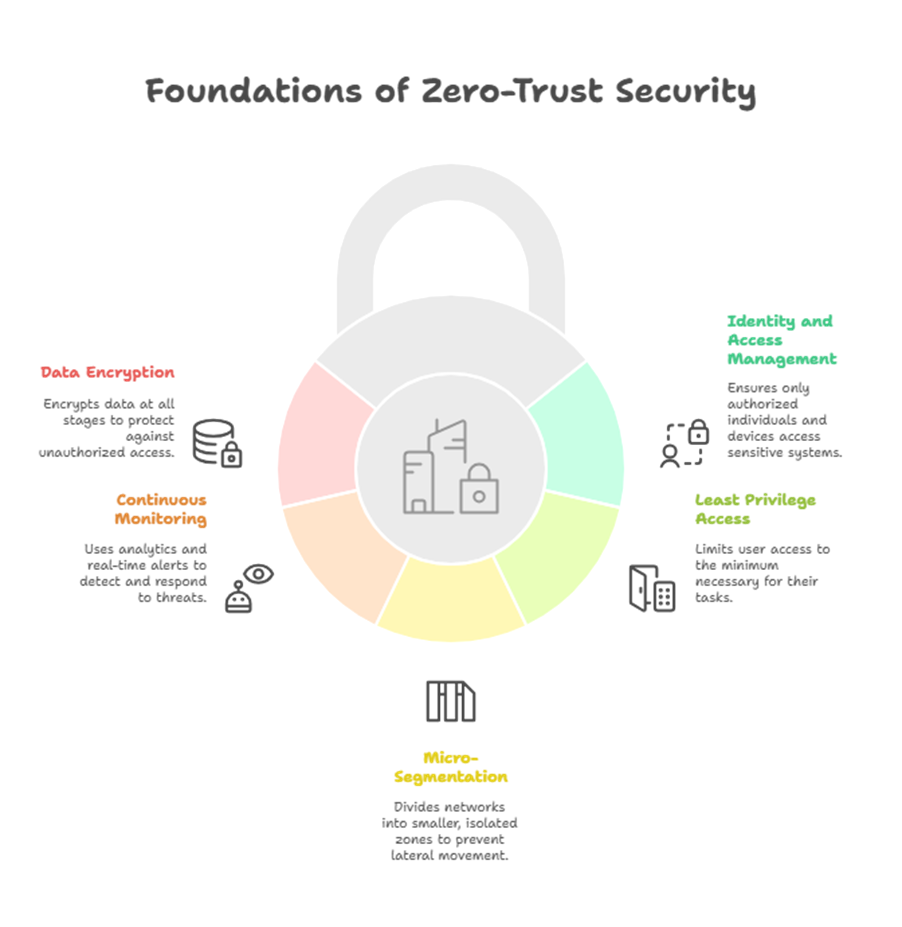
The following fundamental ideas serve as the basis for Techo Lab‘s implementation of zero-trust security models:
1. Management of Identity and Access (IAM)
Authorization, authentication, and ongoing validation are required for each person and device. Make sure that only the appropriate individuals have access to sensitive systems by integrating techniques like role-based access, MFA, and SSO.
2. Access with Least Privilege
Allow users just the minimal amount of access necessary to complete their tasks. In the event of a breach, this restricts the harm.
3. Small-scale division
Segment cloud environments and networks into discrete, smaller areas. An attacker cannot migrate laterally across your systems, even if they manage to compromise one zone.
4. Constant Analytics and Monitoring
To keep an eye on access trends and react quickly to threats, use behavior analytics, anomaly detection, and real-time notifications.
5. Encrypt All Data
Encrypting data while it’s in motion, at rest, and while being processed is recommended. This guarantees that hackers cannot use even intercepted data.
How Techo Lab Gives Clients Zero-Trust
We implement, not just consult. Our security professionals at Techo Lab tackle each organization’s environment differently:
- Complete network and application audit
- Design and implementation of the IAM architecture
- Setting up zero-trust policies on-premises and in the cloud
- Integrating monitoring tools such as Azure AD, Okta, and CrowdStrike
- Exercises simulating threats and staff training
We prioritize business-aligned security, making sure that performance isn’t sacrificed for protection.
Typical Errors (and How to Avoid Them)
Making the switch to a Zero-Trust model is a cultural as well as a technological one. Teams frequently make the following errors:
- Believing that tools by themselves are sufficient—Zero-Trust is a strategy, not only a stack.
- Making access policies too complicated: start small and make adjustments as needed.
- Ignoring user experience: Secure systems need to remain functional.
- Ignoring leadership support A key component of long-lasting reform is executive alignment.
With staged rollouts and quantifiable milestones, Techo Lab assists enterprises in avoiding these pitfalls.
Concluding remarks
Zero-Trust Security Models are the way of the future for business protection, not just a trendy term. Adopting a Zero-Trust strategy in 2025 will be essential to safeguarding your operations, users, and reputation as threats change and digital ecosystems grow.
The moment to act is now, regardless of whether you are a cloud-based SaaS platform, healthcare provider, or startup.
Techo Lab can assist you in creating and putting into practice a Zero-Trust architecture that offers genuine security without impeding your company’s operation





